An advanced Enterprise Job Scheduler designed to automate intricate job scheduling tasks across any mid-range platform, database and application. This powerful portable batch system offers centralized job scheduling management and remote control capabilities, capable of streamlining all scheduling processes across your entire organization worldwide. The Enterprise Job Scheduler supports native installation in every midrange environment, including IBM i (iSeries AS400), Windows, Linux, AIX, HP-UX and Solaris environments - ensuring optimal throughput, accuracy and efficiency. The Enterprise Job Scheduler serves as a portable batch system which can be used for single platform use cases, such as an IBM i job scheduler, offering a...
Protecting the IBM i Integrated File System IFS from ransomware and other forms of malware can be a fairly quick process, and there are a number of simple steps you can take to minimize your systems’ vulnerabilities to prevent a successful attack. You should be aware, viruses, ransomware and other forms of malware do not run on the IBM i, however these threats can severely wreak havoc on the IBM i as a result of a few common security vulnerabilities that can often be resolved with a few simple changes. Other IBM i environments will have to take additional security measures...
Screen Capture for IBM i is a feature of the Authority Manager that automates monitoring users performing sensitive tasks or those needing special authorities to perform specific tasks in a controlled and fully auditing environment. The IBM i Screen Capture feature takes a screen shot of each screen the user is on and includes all the user entered text, and saves the screen shot in a searchable pdf and log on the IBM i. The IBM i Authority Manager enables monitoring powerful users via rules that ensures ticket numbers are used for assigned tasks, auditing and screen capture is enabled, and...
IBM uses three key lifecycle milestones when they discuss support for hardware products. End of Marketing (EOM), End of Support (EOS), and End of Life (EOL). These terms define when a system is no longer sold, when IBM winds down official support, and when it reaches the absolute end of its support. Knowing these distinctions helps businesses plan upgrades, extend warranties, and maintain system reliability. End of Marketing (EOM): No Longer Available for Purchase What it means: IBM stops selling a specific System or Feature. This means new units can no longer be purchased directly from New from IBM. Impact: Existing users...
IT can be a double-edged sword for growing businesses. On one hand, it’s critical to operations and growth. On the other, managing increasingly complex infrastructure can tie up time, resources, and budgets. Instead of driving progress, inefficient IT systems often hold businesses back, keeping their teams stuck in maintenance mode instead of focusing on what really matters: growth, innovation, and delivering results. The good news? IBM Power10 changes that dynamic. Built with efficiency, automation, and performance in mind, Power10 simplifies IT in ways that save businesses time, money, and resources. Here are 4 reasons why upgrading to Power10 can make a...
Downtime isn’t just inconvenient—it can be catastrophic. From natural disasters to cyberattacks and hardware failures, businesses face a growing number of threats that can disrupt operations, damage reputations, and lead to significant financial losses. That’s why having a resilient business continuity strategy isn’t just a good idea—it’s essential. Learn more about the real costs of a data breach in our blog. So, where do you start? Building a robust business continuity plan may seem daunting but breaking it down into manageable steps can make all the difference. Here are five key steps to create a strategy that keeps your business running...
We get it—upgrading your IT systems probably isn’t at the top of your to-do list. If your current legacy systems are working “well enough,” it’s easy to put off change. But here’s the truth: those older systems are costing your business more than you realize. Between unexpected downtime, rising maintenance bills, and serious security risks, sticking with outdated systems can hold you back while quietly eating away at your bottom line. So, what’s the better option? IBM Power10. Upgrading to IBM Power10 can give your business a massive performance boost, strengthen security, and even save you money in the long run. Let’s break...
Data breaches are no longer a hypothetical risk; they’re a costly reality for organizations across industries. IBM’s 2023 Cost of a Data Breach Report highlights the severity of the problem, including revealing that the global average cost of a breach in 2023 reached $4.45 million. Beyond the financial damage, breaches disrupt operations, tarnish reputations, and leave lasting legal and compliance challenges. The report found that at the heart of many of these breaches lies a glaring vulnerability: user access security. Phishing attacks and compromised login credentials—often interconnected—remain the top causes of data breaches. Addressing these vulnerabilities isn’t just a best practice;...
Purchasing an IBM Power10 server is an investment in your business's future. With its power, security, and scalability, this server is built to handle modern workloads effortlessly. However, a server’s potential doesn’t end at its configuration. For maximum return on investment, you need a partner who can handle the details beyond the hardware—ensuring smooth deployment, reliable support, and proactive cost management. That’s where Midland comes in. As an IBM Gold Business Partner, Midland’s expertise and white-glove services empower your business to unlock the full capabilities of Power10. Here’s how we go beyond system configuration to deliver long-term value. 1. Evaluate...
Upgrading your IT infrastructure doesn’t have to be a headache. At Midland, we’re here to take the stress out of the process and ensure you get the right solution for your business. Whether you're considering an IBM Power10 upgrade to boost performance and scalability or simply looking to maximize your investment, we make it straightforward, efficient, and hassle-free. With our expert guidance and the right preparation, your first call with Midland can set the stage for a smooth upgrade experience. Here’s everything you need to know to get started—and how we’ll help make the process seamless every step of...
The ability to adapt to changing technology needs isn’t a luxury—it’s a necessity. Enterprises are increasingly embracing hybrid environments, combining the utilization of on-premises infrastructure, private cloud, and public cloud services, with orchestration between these platforms. Unlike a fully cloud-native model, hybrid environments offer businesses the best of both worlds: the security and control of on-premises systems and the agility and scalability of cloud computing. Disaster Recovery Made SimpleOne of the standout benefits of hybrid environments is improved disaster recovery. In a traditional on-premises setup, a hardware failure or local disaster could bring business operations to a halt. With a...
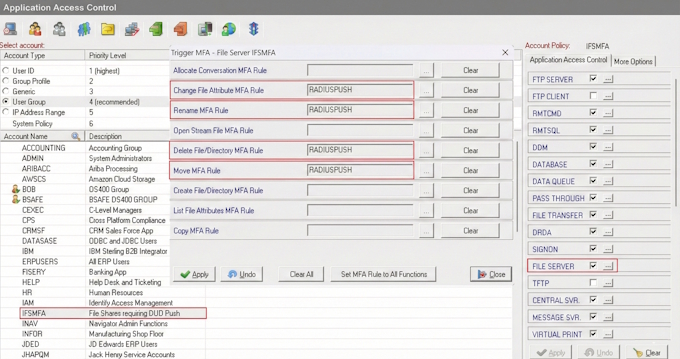
AS400 Firewall Manager is a software based firewall that runs natively on the IBM i that enables administrators to define incoming and outgoing access policies based on Ports, IP Addresses, and logical groups of which AS400 Network Segmentation policies can be applied for the types of traffic that may flow in and out of the IBM i. The AS400 Firewall Manager uses AS400 exit programs to control traffic, and provides a simple point and click GUI interface to define policies. The AS400 exit program for the QIBM_QSO_ACCEPT exit point is used to monitor and control incoming traffic and a separate exit...
IBM has recently shifted to a subscription pricing model for its Power10 systems, marking a significant change from their traditional perpetual licensing approach. Here are the key details about IBM's new Power10 subscription pricing model. Subscription Model Overview IBM now offers subscription-based pricing for Power10 systems running IBM i, available on all Power9 and Power10 servers. This model covers the core license, users, zero-dollar Licensed Program Products (LPPs), and software maintenance. Pricing Tiers The pricing structure is divided into different tiers based on the system size: P05 and P10 Tiers These tiers have per-user charges and unlimited 5250 Enterprise Enablement greenscreen...
IBM has introduced a new subscription-based pricing model for its Power10 systems, marking a significant shift from the traditional perpetual licensing model. This change aims to provide more flexibility and cost-effectiveness for businesses adopting IBM Power10 technology. Power 10 Subscription Pricing Model The new pricing structure for IBM Power10 is tiered and subscription-based. This model allows businesses to pay for the resources they need on a more flexible basis, rather than making a large upfront investment. General Power 10 Pricing Tiers As of April 2024, the annual pricing for subscription-based IBM Power10 includes: OS Licensing: Non-expiring: $15,895Subscription: $8,925 Users (10s): Non-expiring:...
Table of Contents 1. Executive Summary 2. Architectural Evolution: Power9 → Power10 3. Core & SMT Differences 4. Performance per Watt and Efficiency 5. Memory, I/O, and Encryption 6. Real-World Enterprise Case Studies 7. Total Cost of Ownership & Licensing 8. Migration Considerations: Power9 → Power10 9. Final Takeaways for IT Decision-Makers 1. Executive Summary IBM Power10 delivers markedly higher performance and efficiency compared to Power9—typically 20–30% more performance per core, and up to 2.6× better performance per watt. It brings new encryption, AI inference, and virtualization capabilities. However, upgrading requires architecture planning, cost evaluation, and alignment with workload characteristics. 2....
Table Of Contents Chapter 1: Introduction to Managed SIEM 7 What is Managed SIEM? 7 Benefits of Managed SIEM 10 Challenges in Implementing Managed SIEM 13 Role of Managed SIEM in Cybersecurity 15 Chapter 2: Managed SIEM - Definition & Overview 18 Understanding SIEM (Security Information and Event Management) 18 Evolution of Managed SIEM 20 Key Components of Managed SIEM 24 How Managed SIEM Works 27 Advantages of Managed SIEM over In-house Solutions 29 Chapter 3: Cloud Managed SIEM 32 Introduction to Cloud Managed SIEM 32 Benefits of Cloud Managed SIEM 33 Challenges in Implementing Cloud Managed SIEM 34 Features and...
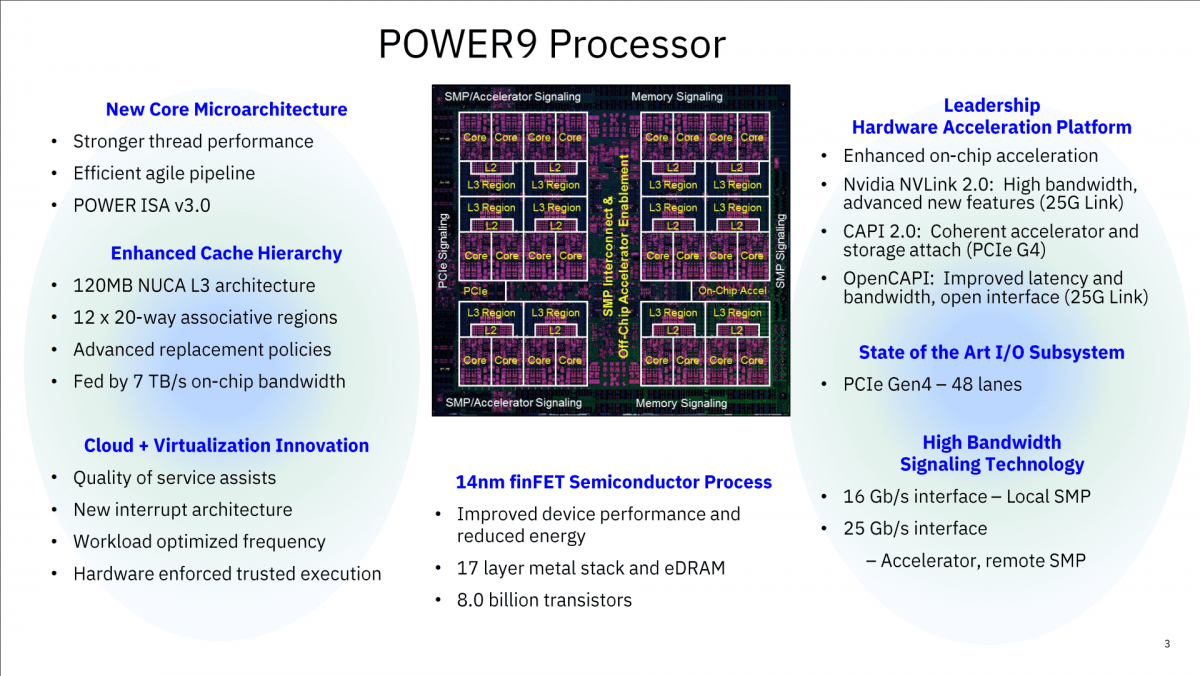
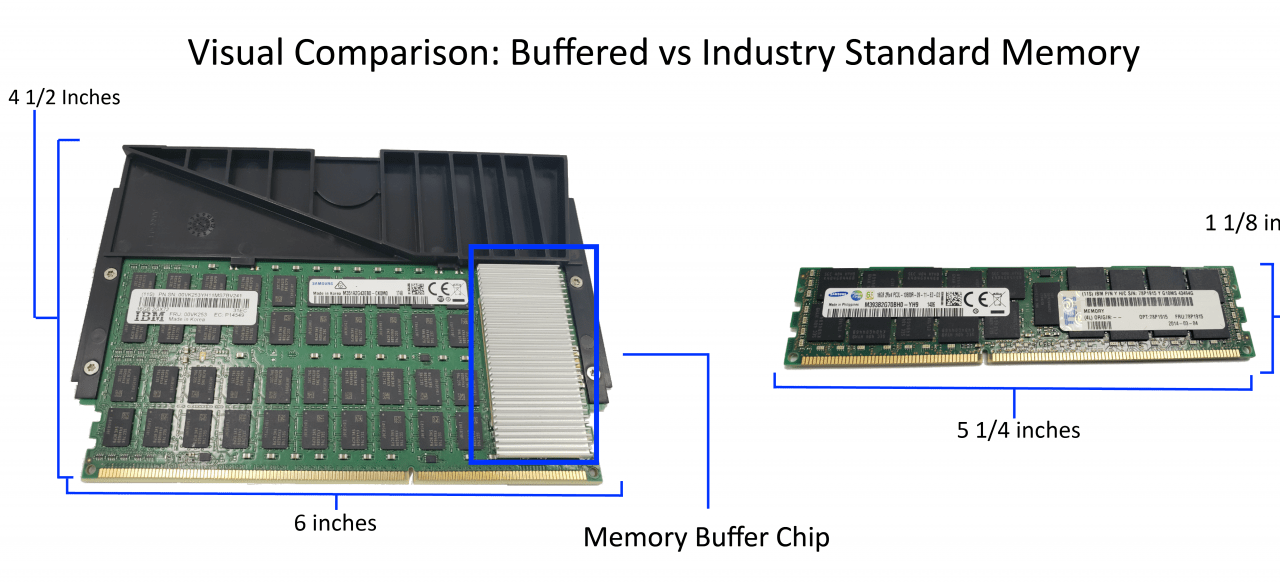
Nigel Griffiths presents 10 useful facts about performance, history and architecture of IBM's Power9 S924 System CPUs. Nigel works for IBM Advanced Technology Support, Europe. His job is to promote IBM Power Systems, PowerVM and AIX Technology. He not an IBM spokesperson. All opinions are his own. IBM Power9 S924 FAQs 1 or 2 sockets for 1 or 2 POWER9 ChipsEach POWER9 Chip has 8, 10 or 12 CPU cores2 socket servers have 16, 20 or 24 CPU coresEach CPU core runs 8 programs at a time (SMT=8)The server runs 192 programs at the same timeEach POWER9 chip has 8 billion transistorsLithography 14nm –...
Understanding Performance Metrics Before diving into optimization strategies, it's essential to understand the key performance metrics that impact the overall health of an IBM i system. Some of the critical metrics include: CPU Utilization: Monitoring CPU usage helps identify potential bottlenecks and ensures that the processor is efficiently utilized. Memory Usage: Managing memory effectively is crucial for preventing performance degradation. Monitoring memory consumption and addressing memory leaks is essential. Disk I/O: Tracking disk I/O operations helps identify potential issues with storage and optimize data access. Network Throughput: Monitoring network performance is vital, especially in distributed environments, to ensure smooth communication between...
Every investment counts, especially in this era of dynamic AI driven tech. Choosing the right computing infrastructure is pivotal.IBM Power10, with its robust performance and scalability, offers a tailored solution for small enterprises.This article delves into the pricing strategies for IBM Power10, providing insights into three example configurations aimed at optimizing cost efficiency. Understanding IBM Power10 Pricing Models IBM Power10 pricing models are designed to cater to a diverse range of business needs. The flexibility of these models allows small businesses to tailor their infrastructure to specific requirements while ensuring cost-effectiveness. Let's explore three example configurations, each crafted to meet different...
IBM FlashSystem is a family of all-flash storage solutions designed and manufactured by IBM. These systems are designed to provide high-performance, low-latency storage for enterprise-level applications and workloads. IBM FlashSystem products leverage solid-state drive (SSD) technology to deliver faster data access and improved storage efficiency compared to traditional spinning hard disk drives (HDDs). Midland IBM FlashSystems Flash Storage Products IBM FlashSystem Guarantee Cybersecurity Protection IBM FlashSystem 5000 FS5015 2072-2N2 2072-2N4 Flash Storage IBM FlashSystem 5000 FS5035 2072-3N2 2072-3N4 Flash Storage IBM 5100 FS5015 2072 2N2 2N4 FlashSystem IBM FlashSystem 5200 FS5200 4662-6H2 Flash Storage Key features and benefits of IBM FlashSystem...