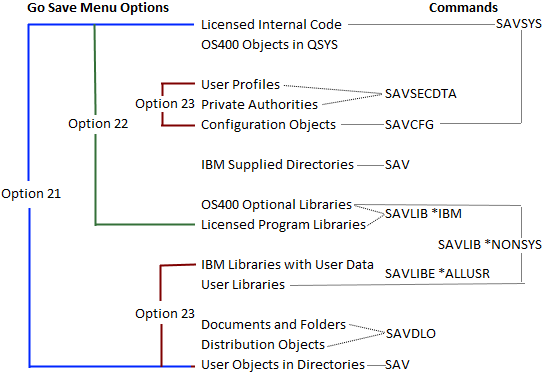
Immutable backup technology is a critical component for Cyber Resiliency and Disaster Recovery for organizations of any size. As for an IBM i backup copy, there are additional options for immutable backups and SafeGuarded Copy solutions. Cyber resilience is a measure of an organization’s ability to protect data and continue business operations despite a successful cyberattack involving data that is either corrupted or destroyed, such as from a malware or ransomware attack. The measure of cyber resiliency is based on amount of data loss and recovery time required to resume normal business operations. If you were to conduct a cyber resiliency...
IBM i backup performance is affected by many variables, and many data transfer rate bottlenecks can be very easy to resolve. Some simple changes you can try to improve IBM i backup performance may only require simple changes like using the correct media generation for your tape library or tape drive, minimize resource sharing, shortening the distance between the IBM i PCIe I/O adapter and tape library/drive, using backup optimization settings or restructuring your backup processes. These minor changes are virtually free to try and may have a significant impact on optimizing your IBM i backup transfer rates and without having...
Protecting the IBM i Integrated File System IFS from ransomware and other forms of malware can be a fairly quick process, and there are a number of simple steps you can take to minimize your systems’ vulnerabilities to prevent a successful attack. You should be aware, viruses, ransomware and other forms of malware do not run on the IBM i, however these threats can severely wreak havoc on the IBM i as a result of a few common security vulnerabilities that can often be resolved with a few simple changes. Other IBM i environments will have to take additional security measures...
An advanced Enterprise Job Scheduler designed to automate intricate job scheduling tasks across any mid-range platform, database and application. This powerful portable batch system offers centralized job scheduling management and remote control capabilities, capable of streamlining all scheduling processes across your entire organization worldwide. The Enterprise Job Scheduler supports native installation in every midrange environment, including IBM i (iSeries AS400), Windows, Linux, AIX, HP-UX and Solaris environments - ensuring optimal throughput, accuracy and efficiency. The Enterprise Job Scheduler serves as a portable batch system which can be used for single platform use cases, such as an IBM i job scheduler, offering a...
IBM Hardware End of Service Updates On May 31st, 2024 IBM will be ending hardware support for all Power8 systems. After that date, IBM will continue the support with a hardware service extension. This hardware service extension will be an additional fee that will be as high as 70% or more of the existing hardware maintenance. This fee is included in current quotes that will renew later than 5/31/2024. On October 20th, 2023 IBM will be withdrawing all Power9 systems and will no longer be shipping them. IBM Software End of Service Updates As of September 30th, 2023 IBM is ending...
Screen Capture for IBM i is a feature of the Authority Manager that automates monitoring users performing sensitive tasks or those needing special authorities to perform specific tasks in a controlled and fully auditing environment. The IBM i Screen Capture feature takes a screen shot of each screen the user is on and includes all the user entered text, and saves the screen shot in a searchable pdf and log on the IBM i. The IBM i Authority Manager enables monitoring powerful users via rules that ensures ticket numbers are used for assigned tasks, auditing and screen capture is enabled, and...
IBM uses three key lifecycle milestones when they discuss support for hardware products. End of Marketing (EOM), End of Support (EOS), and End of Life (EOL). These terms define when a system is no longer sold, when IBM winds down official support, and when it reaches the absolute end of its support. Knowing these distinctions helps businesses plan upgrades, extend warranties, and maintain system reliability. End of Marketing (EOM): No Longer Available for Purchase What it means: IBM stops selling a specific System or Feature. This means new units can no longer be purchased directly from New from IBM. Impact: Existing users...
IT can be a double-edged sword for growing businesses. On one hand, it’s critical to operations and growth. On the other, managing increasingly complex infrastructure can tie up time, resources, and budgets. Instead of driving progress, inefficient IT systems often hold businesses back, keeping their teams stuck in maintenance mode instead of focusing on what really matters: growth, innovation, and delivering results. The good news? IBM Power10 changes that dynamic. Built with efficiency, automation, and performance in mind, Power10 simplifies IT in ways that save businesses time, money, and resources. Here are 4 reasons why upgrading to Power10 can make a...
Downtime isn’t just inconvenient—it can be catastrophic. From natural disasters to cyberattacks and hardware failures, businesses face a growing number of threats that can disrupt operations, damage reputations, and lead to significant financial losses. That’s why having a resilient business continuity strategy isn’t just a good idea—it’s essential. Learn more about the real costs of a data breach in our blog. So, where do you start? Building a robust business continuity plan may seem daunting but breaking it down into manageable steps can make all the difference. Here are five key steps to create a strategy that keeps your business running...
We get it—upgrading your IT systems probably isn’t at the top of your to-do list. If your current legacy systems are working “well enough,” it’s easy to put off change. But here’s the truth: those older systems are costing your business more than you realize. Between unexpected downtime, rising maintenance bills, and serious security risks, sticking with outdated systems can hold you back while quietly eating away at your bottom line. So, what’s the better option? IBM Power10. Upgrading to IBM Power10 can give your business a massive performance boost, strengthen security, and even save you money in the long run. Let’s break...
Data breaches are no longer a hypothetical risk; they’re a costly reality for organizations across industries. IBM’s 2023 Cost of a Data Breach Report highlights the severity of the problem, including revealing that the global average cost of a breach in 2023 reached $4.45 million. Beyond the financial damage, breaches disrupt operations, tarnish reputations, and leave lasting legal and compliance challenges. The report found that at the heart of many of these breaches lies a glaring vulnerability: user access security. Phishing attacks and compromised login credentials—often interconnected—remain the top causes of data breaches. Addressing these vulnerabilities isn’t just a best practice;...
Purchasing an IBM Power10 server is an investment in your business's future. With its power, security, and scalability, this server is built to handle modern workloads effortlessly. However, a server’s potential doesn’t end at its configuration. For maximum return on investment, you need a partner who can handle the details beyond the hardware—ensuring smooth deployment, reliable support, and proactive cost management. That’s where Midland comes in. As an IBM Gold Business Partner, Midland’s expertise and white-glove services empower your business to unlock the full capabilities of Power10. Here’s how we go beyond system configuration to deliver long-term value. 1. Evaluate...
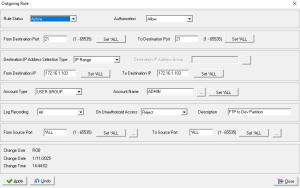
AS400 Firewall Manager is a software based firewall that runs natively on the IBM i that enables administrators to define incoming and outgoing access policies based on Ports, IP Addresses, and logical groups of which AS400 Network Segmentation policies can be applied for the types of traffic that may flow in and out of the IBM i. The AS400 Firewall Manager uses AS400 exit programs to control traffic, and provides a simple point and click GUI interface to define policies. The AS400 exit program for the QIBM_QSO_ACCEPT exit point is used to monitor and control incoming traffic and a separate exit...
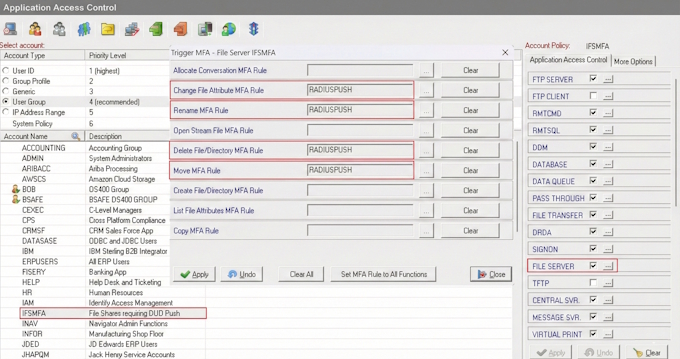
IBM i Two-Factor Authentication (2FA) is a quick and simple to implement Multi-Factor Authentication solution that ensures a user’s identity before granting access to critical or sensitive data on your system. IBM i 2FA can be enforced for various connection types, including interactive 5250 telnet signon sessions, and for most TCP/IP connections where users logon thru an exit point, such Database Server for ODBC and JDBC connections, Signon Server, FTP Server and File Server for accessing the IFS, which can help prevent ransomware and other forms of malware from damaging your system. IBM i MFA can also be used for securing SSH...
IBM V7R5 Technology Refresh 1 TR1 builds on the simplicity of integration theme in the IBM i 7.5.0 base release, and includes many fixes and enhancements that improve performance of IBM i Power10 and Power9 servers as explained in the memo to IBM i customers. The IBM V7R5 TR1 enhancements and new functions released on December 2, 2022 are explained in this article below. IBM i 7.5 TR1 has been designated MF99401 PTF in PTF Group Level is SF99957, and has RS-750-B Resave Level and RE22291 PTF Marker. IBM V7R5 TR2 enhancements and new functions are explained in a separate article,...
IBM Power9 Systems and features below are only available in refurbished or used condition, and are no longer sold in new condition by IBM as specified by below dates. The IBM Power9 withdrawn systems and features from marketing are listed below, but can still be placed under an IBM Hardware Maintenance HWMA at standard rates. The below list of IBM Power9 systems and features do not have an end of life, end of service or end of support date specified by IBM. Midland will continue to sell IBM Power9 Server models, features, and parts in used and refurbished condition. All used and...
IBM i 7.4 TR2 Details: V7R4 Technology Release 2 Announcement for 5770-SS1 IBM i V7R4 TR2 Technology Release 2 for IBM POWER9 and POWER8 Systems with OS400 was announced on May 15, 2020, adding many new enhancements for security, encryption, virtualization, high availability, backup and recovery, web services, DB2 database, administration, architecture, APIs, development and many other major improvements that affect operating system components, software licenses and hardware features. Read about IBM V7R5 announcement details here. IBM i 7.4 TR2 is supported on select Power Systems servers with POWER9 or POWER8 processors and OS400 operating systems. IBM i customers using Blades,...
Security detection and response that is not automated or real-time, is simply not providing protection and is not security at all. You should already know which SIEM features are most important to improve your security posture. Automation and Real-time Detection and Response are the key for security. Now it’s just a matter of finding which SIEM delivers on all its promises. Odds are, you are not satisfied with your SIEM and perhaps feel you have invested in the wrong solution. Depending on the SIEM vendor, you may even feel trapped, and must continue with the limited options from your current vendor....
IBM Flash System Storage is an inexpensive start in a cyber resilience solution that simplifies and futureproofs business continuity. Now that’s business continuity made easy!
What to Look for in an Endpoint Security, EDR SolutionLegacy endpoint security tools are no match for today’s malware and ransomware attacks. Attackers are well aware of the protection methods that outdated EDR solutions are using, and renders them useless. Attackers have studied these tools for years and know exactly how to by-pass them, and in some cases disables them entirely. Outdated endpoint security tools are looking for well-known criteria, which is exactly why endpoints are still attackers favorite and easiest targets. If your endpoint security defenses cannot evolve as fast as the ransomware mutates, you simply cannot protect against the...