Understanding Performance Metrics Before diving into optimization strategies, it's essential to understand the key performance metrics that impact the overall health of an IBM i system. Some of the critical metrics include: CPU Utilization: Monitoring CPU usage helps identify potential bottlenecks and ensures that the processor is efficiently utilized. Memory Usage: Managing memory effectively is crucial for preventing performance degradation. Monitoring memory consumption and addressing memory leaks is essential. Disk I/O: Tracking disk I/O operations helps identify potential issues with storage and optimize data access. Network Throughput: Monitoring network performance is vital, especially in distributed environments, to ensure smooth communication between...
Used IBM Servers | New Power 10 Systems | QRadar SIEM Security
🔊 Read by AI Larry Every investment counts, especially in this era of dynamic AI driven tech. Choosing the right computing infrastructure is pivotal.IBM Power10, with its robust performance and scalability, offers a tailored solution for small enterprises.This article delves into the pricing strategies for IBM Power10, providing insights into three example configurations aimed at optimizing cost efficiency. Understanding IBM Power10 Pricing Models IBM Power10 pricing models are designed to cater to a diverse range of business needs. The flexibility of these models allows small businesses to tailor their infrastructure to specific requirements while ensuring cost-effectiveness. Let's explore three example...
IBM FlashSystem is a family of all-flash storage solutions designed and manufactured by IBM. These systems are designed to provide high-performance, low-latency storage for enterprise-level applications and workloads. IBM FlashSystem products leverage solid-state drive (SSD) technology to deliver faster data access and improved storage efficiency compared to traditional spinning hard disk drives (HDDs). Midland IBM FlashSystems Flash Storage Products IBM FlashSystem Guarantee Cybersecurity Protection IBM FlashSystem 5000 FS5015 2072-2N2 2072-2N4 Flash Storage IBM FlashSystem 5000 FS5035 2072-3N2 2072-3N4 Flash Storage IBM 5100 FS5015 2072 2N2 2N4 FlashSystem IBM FlashSystem 5200 FS5200 4662-6H2 Flash Storage Key features and benefits of IBM FlashSystem...
IBM Hardware End of Service Updates On May 31st, 2024 IBM will be ending hardware support for all Power8 systems. After that date, IBM will continue the support with a hardware service extension. This hardware service extension will be an additional fee that will be as high as 70% or more of the existing hardware maintenance. This fee is included in current quotes that will renew later than 5/31/2024. On October 20th, 2023 IBM will be withdrawing all Power9 systems and will no longer be shipping them. IBM Software End of Service Updates As of September 30th, 2023 IBM is ending...
IBM Power9 Systems and features below are only available in refurbished or used condition, and are no longer sold in new condition by IBM as specified by below dates. The IBM Power9 withdrawn systems and features from marketing are listed below, but can still be placed under an IBM Hardware Maintenance HWMA at standard rates. The below list of IBM Power9 systems and features do not have an end of life, end of service or end of support date specified by IBM. Midland will continue to sell IBM Power9 Server models, features, and parts in used and refurbished condition. All used and...
IBM Power8 End of Life EOL a.k.a End of Support Service EOS IBM Power8 Servers are being withdrawn from service for IBM Maintenance and Support, and will also discontinue leases and rentals. As of July 17, 2023, standard IBM Hardware Maintenance HWMA for IBM Power8 models can no longer be purchased. Midland however will continue to sell used and refurbished IBM Power8 Servers, parts and related extended maintenance and support service agreements to customers. All used and refurbished IBM i and IBM AIX Power hardware sold by Midland includes warranty and support, and optional extended maintenance and support agreements can also...
IBM V7R5 Technology Refresh 1 TR1 builds on the simplicity of integration theme in the IBM i 7.5.0 base release, and includes many fixes and enhancements that improve performance of IBM i Power10 and Power9 servers as explained in the memo to IBM i customers. The IBM V7R5 TR1 enhancements and new functions released on December 2, 2022 are explained in this article below. IBM i 7.5 TR1 has been designated MF99401 PTF in PTF Group Level is SF99957, and has RS-750-B Resave Level and RE22291 PTF Marker. IBM V7R5 TR2 enhancements and new functions are explained in a separate article,...
IBM V7R5 (7.5) was released on May 10, 2022 Enhancements include new features to the base OS400 operating system, DB2 Database, IBM i license programs and support for additional Open Source solutions. IBM i V7R5 is supported by IBM i Power10, Power9 Systems and future IBM Power System models. This article will explain the details of each enhancement and new feature available with the initial IBM V7R5 release. The successive V7R5 Technology Refresh releases will be explained in detail in separate articles. IBM V7R5 TR1 was released on December 2, 2022, and IBM V7R5 TR2 was released on May 5, 2023. IBM...
Security detection and response that is not automated or real-time, is simply not providing protection and is not security at all. You should already know which SIEM features are most important to improve your security posture. Automation and Real-time Detection and Response are the key for security. Now it’s just a matter of finding which SIEM delivers on all its promises. Odds are, you are not satisfied with your SIEM and perhaps feel you have invested in the wrong solution. Depending on the SIEM vendor, you may even feel trapped, and must continue with the limited options from your current vendor....
IBM Flash System Storage is an inexpensive start in a cyber resilience solution that simplifies and futureproofs business continuity. Now that’s business continuity made easy!
IBM i SIEM Security Event Logs for MonitoringCompanies using Splunk, QRadar or any other SIEM to monitor security incidents, of which also run core business applications on an IBM i, should be forwarding specific data sets and event log sources to their SIEM. Most companies with an IBM i (AS400 or iSeries), often have their most critical business applications running on it, yet the AS400 is commonly the last platform to be added to the SIEM. Security Operation Center Administrators and Architects often underestimate the importance the AS400 and its underlying applications are to their company, or disregard it due to...
What to Look for in an Endpoint Security, EDR SolutionLegacy endpoint security tools are no match for today’s malware and ransomware attacks. Attackers are well aware of the protection methods that outdated EDR solutions are using, and renders them useless. Attackers have studied these tools for years and know exactly how to by-pass them, and in some cases disables them entirely. Outdated endpoint security tools are looking for well-known criteria, which is exactly why endpoints are still attackers favorite and easiest targets. If your endpoint security defenses cannot evolve as fast as the ransomware mutates, you simply cannot protect against the...
IBM AIX Power systems are enterprise-class open standards-based Unix servers that support critical applications and database workloads having high I/O and memory requirements, and require maximum performance, availability, security and scalability. IBM’s AIX Power systems have been the most popular Unix server line in the world for over a decade for a number of compounding reasons. As a whole, IBM’s AIX Power server platform has countless industry leading benchmarks and application specific achievements that attrct businesses for specific uses cases, but after factoring in software license costs, the total cost of ownership numbers makes the IBM Power platform the obvious choice....
Immutable backup technology is crtical component for Cyber Resiliency and Disaster Recovery for organizations of any size. Cyber resilience is a measure of an organization’s ability to protect data and continue business operations despite a successful cyberattack involving data that is either corrupted or destroyed, such as from a malware or ransomware attack. The measure of cyber resiliency is based on amount of data loss and recovery time required to resume normal business operations. If you were to conduct a cyber resiliency analysis of your environment based on NIST CSF, it would assesses and score your organization’s readiness to sustain and...
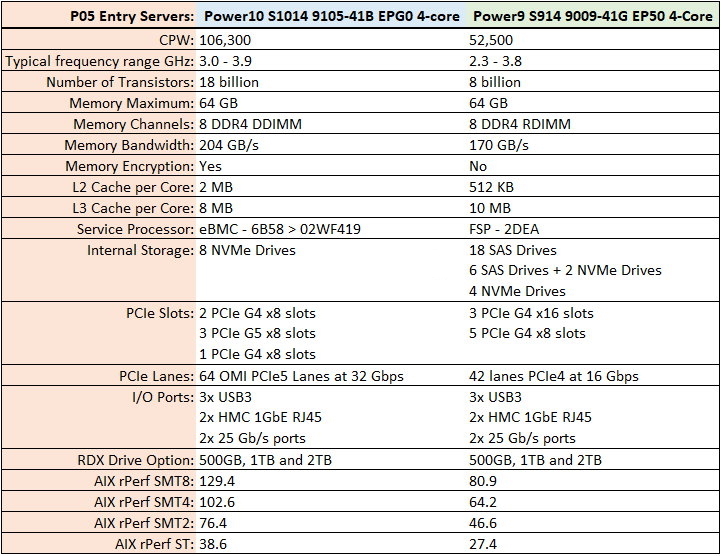
The IBM S1014 9105-41B EPG0 4-core Processor is the most popular Power10 model for AS400 workloads, which is not surprising considering the amount of CPW IBM added for the new entry P05 software tier system. The IBM i S1014 9105-41B EPG0 4-core processor has a whopping 106,300 CPW, and that is a lot of power for the SMB market to take advantage of. IBM more than doubled the CPW for the new Power10 S1014 4-core IBM i entry model, which is an astonishing increase in comparison to the previous fastest P05 Power9 processor system, the IBM S914 9009-41G EP50 4-Core that...
We said good bye today to a very dear friend and family member Henry Rodriguez. It was a beautiful ceremony for a truly beautiful person. Henry was loved by everyone that knew him, which showed by the huge turnout. People flew in and drove to Florida from all over the country. Those that had the opportunity to stand up to speak about him, knew exactly what to say. Even if I were asked to speak, I do not know how I would have gotten through it. The entire place had to be tears after hearing his sweet little daughter Oliva speak...