AI Cybersecurity SIEM QRadar Vulnerability Scanner
AI cybersecurity SIEM security information event management solution by QRadar provides vulnerability and risk analysis of network devices, applications and systems within the DMZ, presents a consolidated view of discovered weaknesses from network scans and event logs, and identifies required configuration changes, updates and patches needed for remediation. Monitoring and managing network vulnerabilities and risks is an overwhelming task for most companies, where network scan results can reveal thousands of risks and exposures, creating a complex puzzle of misconfigured devices, software updates and patches needed to prevent cybersecurity attacks and breaches. The volume of threats found the SIEM is growing each day, becoming more sophisticated and are designed to go unnoticed, which the increasing rate of disclosed security breaches accurately reflects.
QRadar SIEM integrates AI cybersecurity, machine learning, security threat feeds, user behavior analytics and vulnerability scans in conjunction with event logs and network traffic logs, to automate the costly and time consuming manual tasks of threat hunting, vulnerability monitoring, risk detection and identifying abnormal or unauthorized activities. QRadar Vulnerability Manager (QVM) is included in its SIEM Security solutions, and can help organizations reduce network security breaches by continuously scanning for security exposures. The vulnerability scanner has a database of over 70,000 vendor products (routers, firewalls, databases, web servers, web applications, web scripts, custom applications, DNS, mail servers, application servers, wireless access points, common services, systems, obsolete software and obsolete systems) it checks and probes to collect up-to-date results and leverages the capabilities of the QRadar SIEM Security Intelligence Platform to present the data within the overall context of the network usage, security and threat posture. QVM consolidates results from multiple vulnerability scanners, risk management solutions and external threat intelligence resources, providing centralized control that identify key security weaknesses that need to be addressed to help prevent cybersecurity and internal attacks.
QRadar SIEM also correlates network topology information using data from asset configurations, network event logs and flow patterns, which reveal which assets and vulnerabilities are most at risk, so security analysts can prioritize remediation tasks. QVM can also help identify firewall and intrusion prevention (IPS) misconfigurations that can allow attackers into the network. Many network attacks succeed due to poorly configured network and security policies, emphasizing the need for automated network configuration monitoring and alerts for policy breaches and changes. QRadar Vulnerability Manager provides an integrated, automated, policy enforcement approach that identify security risks through a single console shared with the QRadar SIEM security platform. It leverages a broad range of risk indicators including asset, network and security configuration data, network activity data, network and security events, and vulnerability scan results. It also assigns risk scores, vulnerability risk assessment, and correlation of known vulnerabilities with network topologies, including a prioritized list of vulnerabilities to better assess which systems are most vulnerable to attack and should be remediated first. QRadar Vulnerability Manager also delivers advanced threat modeling, and the simulation and visualization of the potential spread of threats through the network by leveraging vulnerability, network topology and connection data.
QRadar Vulnerability Manager checks for multiple types of vulnerabilities in your network.QRadar Vulnerability Manager checks for multiple types of vulnerabilities in your network. Vulnerabilities are categorized into the following broad categories:
Risky default settings
By leaving some default settings in place, you can make your network vulnerable to attacks. The following situations are examples that can make your network vulnerable:
- Leaving sample pages or scripts on an IIS installation
- Not changing the default password on a 3Com Hub/Switch
- Leaving "public" or "private" as an SNMP community name on an SNMP enabled device
- Not setting the sa login password on an MS-SQL server
Software features
Some software settings for systems or applications are designed to aid usability but these settings can introduce risk to your network. For example, the Microsoft NetBIOS protocol is useful in internal networks, but if it is exposed to the Internet or an untrusted network segment it introduces risk to your network. The following examples are software features or commands that can expose your network to risk:
- ICMP time stamp or netmask requests
- Sendmail expand or verify commands
- Ident protocol services that identify the owner of a running process.
Misconfiguration
In addition to identifying misconfigurations in default settings, QRadar Vulnerability Manager can identify a broader range of misconfigurations such as in the following cases:
- SMTP Relay
- Unrestricted NetBios file sharing
- DNS zone transfers
- FTP World writable directories
- Default administration accounts that have no passwords
- NFS World exportable directories
Vendor flaws
Vendor flaws is a broad category that includes events such as buffer overflows, string format issues, directory transversals, and cross-site scripting. Vulnerabilities that require a patch or an upgrade fix are included in this category.
QRadar Vulnerability Manager helps security teams identify resource configuration issues, understand the impact of software patching schedules, coordinate with intrusion prevention systems to block open connections, and establish continuous monitoring of systems that can’t otherwise be remediated—all from a single, integrated dashboard. QRadar SIEM security intelligence platform is an all-in-one solution, providing AI cybersecurity and internal user threat analysis and intelligence, device configuration with network traffic analysis, and vulnerability manager that can help organizations automate and build actionable security policies quickly using existing security defenses and constrained IT staffing resources.
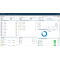
Get a single, prioritized view of potential vulnerabilities
- • Select a dashboard view and click through related tabs to review security offenses, log events, network flows, asset statuses and configurations, reports, risks and vulnerabilities
- • Create, edit and save asset searches and scans for more intelligent monitoring
- • Make faster, more informed decisions with a prioritized, consolidated view of scan data
- • Help coordinate patching and virtual patching activities, and direct intrusion prevention systems (IPSs) to block potential attack paths for maximum impact
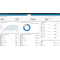
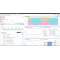
The QRadar Vulnerability Manager topology viewer enables users to view network devices and relationships, including subnets and links QRadar Vulnerability Manager includes an embedded scanning engine that can be set up to run both dynamic and periodic scans, providing near real-time visibility of weaknesses that could otherwise remain hidden. Leveraging the passive asset discovery capabilities of IBM QRadar QFlow and Log Collector appliances, any new asset appearing on the network can be immediately scanned. As a result, organizations can reduce their exposure to advanced threats between regular scanning cycles and help ensure compliance with the latest security regulations.
Using the same rules-based approach as QRadar SIEM, QRadar Vulnerability Manager helps minimize false positives and filters out vulnerabilities already classified as nonthreatening. For example, applications may be installed on a server, but they may be inactive, and therefore not a security risk; devices that appear exposed may actually be protected by a firewall; or endpoints that have vulnerabilities may already be scheduled for patching.
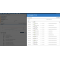
QRadar Vulnerability Manager maintains a current network view of all discovered vulnerabilities, including details such as when the vulnerabilities were found, when they were last seen, what scan jobs reported the vulnerabilities, and to whom the vulnerability is assigned for remediation or mitigation. The software also presents historic views of daily, weekly and monthly trends, and it can produce long-term trending reports, such as the month-by-month trend of Payment Card Industry (PCI) failure vulnerabilities discovered over the past year.
Stand-alone, independent vulnerability-scanning solutions can take considerable time to scan large address spaces for assets, servers and services, and their scan results can be out of date quickly. These point solutions also require additional infrastructure and include different technologies for network, application and database scanning—all requiring additional administration. And after identifying an often incomplete sea of vulnerabilities, the point solutions do not include any contextual information for helping security teams prioritize their tasks for remediation.
Thwart Advanced Threats
Unlike the random, brute-force attacks of the past, today’s organizations must guard against “advanced persistent threats”—that is, a complex series of attacks that often take place over a prolonged timeframe. Using a range of tactics from zero day exploits to custom malware to simply trolling for unpatched systems, these attackers consistently probe their targets using a “low-and-slow” approach until they find a security gap. Organizations can use more intelligent tools like QRadar Vulnerability Manager to improve their defenses by regularly scanning and addressing as many high-impact vulnerabilities as possible.
Most vulnerability scanners simply identify large numbers of exposures and leave it up to security teams to understand the severity of risks. These tools are often not integrated with the existing security infrastructure and require additional manual effort to align with the current network topology, usage information and security processes. Many of these tools are used simply for compliance, rather than as an integral part of a threat and security management program.
Address Compliance Mandates
Regulatory requirements are forcing organizations of all sizes to develop vulnerability management programs to help ensure proper control of sensitive IT assets. QRadar Vulnerability Manager helps organizations facilitate compliance by conducting regular network scans and maintaining detailed audit trails. It categorizes each vulnerability with a severity rating and an exposure score. In addition to scanning assets both internally and externally, QRadar Vulnerability Manager enables security teams to create tickets to manage remediation activities and specify exceptions with a full audit trail.
Extend Your Security Intelligence
QRadar Vulnerability Manager combines the real-time security visibility of QRadar Security Intelligence Platform with the results of proven vulnerability-scanning technology. As part of the QRadar SIEM architecture, QRadar Vulnerability Manager can be deployed quickly and security teams do not need to learn a new interface. They can simply generate reports from within the familiar QRadar family user interface.
Automate Proactive Security:
- High-speed internal scanning, which helps preserve network performance and availability
- Support for discovery, non-authenticated, authenticated and Open Vulnerability Assessment Language (OVAL) scans
- External scanning capabilities to see the network from an attacker’s viewpoint and help facilitate compliance
- Single-click investigations from dashboard screens and deep, rules-based, rapid searching capabilities to learn more about specific events or identify long-term trends
- Suppression of acceptable, false positive or otherwise non-mitigated vulnerabilities from ongoing reporting
- Vulnerability assignment and remediation lifecycle management
- Full audit trail for compliance reporting
Help prevent security breaches by discovering vulnerabilities and risks from a single, integrated dashboard:
- Prioritize remediation and mitigation activities by understanding network context
- Enable seamless integration with IBM Security QRadar SIEM to get dynamic, up-to-date asset information for proactive management of vulnerabilities and risks
- Conduct rapid network scans periodically or dynamically to find security weaknesses and minimize risks
- Visualize current and potential network traffic patterns with a network topology model based on security device configurations
- Quantify and prioritize risks with a policy engine that correlates network topology, asset vulnerabilities, and actual network traffic, enabling risk-based remediation
- Model threat propagation and simulate network topology changes to help improve security
- Centralize network security device management to help reduce configuration errors and simplify monitoring of firewall performance
Why IBM?
IBM Security offers one of the most advanced and integrated portfolios of enterprise security products and services. The portfolio, supported by world-renowned X-Force research and development, provides security intelligence to help organizations holistically protect their people, infrastructures, data and applications, offering solutions for identity and access management, database security, application development, risk management, endpoint management, network security and more. These solutions enable organizations to effectively manage risk and implement integrated security for mobile, cloud, social media and other enterprise business architectures. IBM operates one of the world’s broadest security research, development and delivery organizations, monitors 13 billion security events per day in more than 130 countries, and holds more than 3,000 security patents.
QRadar SIEM Demonstration
QRadar SIEM with integrated Cybersecurity AI
How QRadar SIEM Security is Different from other SIEM Tools
QRadar SIEM Security AI with Watson Advice
QRadar AI Security Machine Learning User Behavior
QRadar SIEM Security Commercial
QRadar SIEM Security Introduction
QRadar SIEM Security Free Apps for Integrating Cisco Security
QRadar SIEM Security Free Apps for Integrating VMware Security
QRadar SIEM integrated Cybersecurity AI - Am I affected Example
QRadar SIEM Machine Learning User Behavior Analytics for Internal Threats
QRadar SIEM Incident Forensics to Stop Security Breaches
SIEM Security and Patch Management are 2 Peas in the same Pod
QRadar SIEM Security as a Service (In the Cloud)
QRadar SIEM Security for Cloud Environments
QRadar using Watson Cybersecurity AI Discovery Service
IBM Managed Security Services MSSP SOC
QRadar SIEM Helps Secure City Government with few IT Resources
QRadar SIEM with embedded Security AI DS
QRadar SIEM Security Machine Learning User Behavior Analytics DS
QRadar SIEM AI Cybersecurity Threat Feeds xForce
QRadar SIEM Security User Behavior Search Analytics DS
QRadar SIEM Vulnerability Scanner DS
QRadar SIEM Security xForce App Exchange DS
SIEM Security MSSP SOC Service Offerings
SIEM Security Product Comparisons
QRadar Scaling, HA, DR Protection
QRadar SIEM Security Customer Feedback
SIEM tools and Security AI Integration WP
Finding Cybersecurity Threats Efficiently WP
AI in Cybersecurity for Security Automation WP
How to Detect and Stop Cybersecurity Threats
Cybersecurity Breaches and Data Theft Cost Study 2018
QRadar SIEM Security Wimbledon CS
QRadar SIEM Security Cargills Bank CS
Optional Add-on Licenses and Services
QRadar SIEM Security Product Line
QRadar SIEM Security Executive Guide
End Point Security Patch Automation DS
End Point Security Patch Automation WP
End Point Security Patch Automation CS
Software License Inventory Management DS
Software License Inventory Management WP
Software License Compliance DS
Software License Compliance WP
QRadar SIEM Cybersecurity Breach Watson Analysis
QRadar SIEM Security Network Traffic Analysis DS
QRadar SIEM Security Network Traffic Analysis WP